Do you feel safe online? You’ve read the stories about hacked bank accounts, stolen identities, online stalkers, and leaked photos. You may wonder who’s listening in on your conversations when you start seeing Facebook ads for a product you were just talking about. It’s creepy.
Can you protect yourself? Yes, there are tools out there. VPNs and TOR are two similar solutions to the problem—one offered commercially by companies, the other a decentralized community project. Both work and are worth checking out.
If you combine the two technologies, you get Onion over VPN. Could that be the ultimate solution? Are there any downsides? Read on to find out how Onion over VPN works and whether it’s for you.

What Is a VPN?
A VPN is a “virtual private network.” Its purpose is to keep your online activities private and secure. That’s important: by default, you’re very visible and very vulnerable.
How visible? Each time you connect to a website, you share information about yourself. That includes:
- Your IP address. Among other things, it lets anyone watching know your internet service provider and approximate location.
- Your system information. That includes your computer’s operating system and browser, CPU, memory, storage space, installed fonts, battery status, number of cameras and microphones, and more.
It’s likely those websites keep a log of that information for every visitor.
Your ISP can also see your online activity. They probably keep logs of every website you visit and how long you spend on each one. If you’re on a business or school network, they probably log that, too. Facebook and other advertisers track you so they know which products to sell you. Finally, governments and hackers can also see and log your connections.
How does that make you feel? I used the word earlier: vulnerable. VPNs use two key strategies to give your privacy back:
- They pass all of your traffic through a VPN server. The websites you visit will log the VPN server’s IP address and location, not your own computer.
- They encrypt all of your traffic from the time it leaves your computer until it arrives at the server. That way, ISP and others are not aware of the websites you visit or the information you send, though they can tell you’re using a VPN.
This makes a significant improvement to your privacy:
- Your employer, ISP, and others can no longer see or log your online activity.
- The websites you visit will log the IP address and location of the VPN server, not your own computer.
- Advertisers, governments, and employers can no longer track you or see the websites you visit.
- You can access content in the server’s country that you may not be able to access from your own.
But there’s one thing you need to be very aware of: your VPN provider can see it all. So choose a service you trust: one with a strong privacy policy that doesn’t keep logs of your activities.
Another thing to be aware of is that using a VPN will affect the speed of your connection. Encrypting your data and passing it through a server takes time. How much time varies depending on your VPN provider, the distance the server is from you, and how many others are using that server at the time.
What Is TOR?
TOR stands for “The Onion Router.” It’s another way to keep your online activities private. TOR isn’t run by or owned by a company or corporation but is a decentralized network run by volunteers.
Instead of using a normal web browser like Safari, Chrome, or Edge, you use the TOR browser, which is available for most operating systems. It protects your privacy and offers benefits similar to a VPN:
1. All of your traffic is encrypted—not just once, but three times. This means that your ISP, employer, and others aren’t aware of your online activity, though they can see that you’re using TOR. Neither will a VPN company.
2. The browser will send your traffic through a random node on the network (a volunteer’s computer), then at least two other nodes before it arrives at the website you want to connect with. The websites you visit won’t know your real IP address or location.
The TOR Project’s official website explains:
Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you’re using Tor.
So TOR is potentially more secure than a VPN, but also slower. Your traffic is encrypted multiple times and passes through more network nodes. It also requires you to use a special web browser.
However, nothing’s perfect. TOR critics feel that VPNs have one advantage: you know who owns the servers. You have no idea who the nodes of the TOR network belong to. Some fear that governments and hackers may volunteer in an effort to track users.
What Is Onion over VPN?
TOR over VPN (or Onion over VPN) is the combination of both technologies. It’s undoubtedly more secure than either technology on its own. But because your traffic runs through both bottlenecks, it’s also slower than either. You’ll gain the most benefit by connecting to your VPN first.
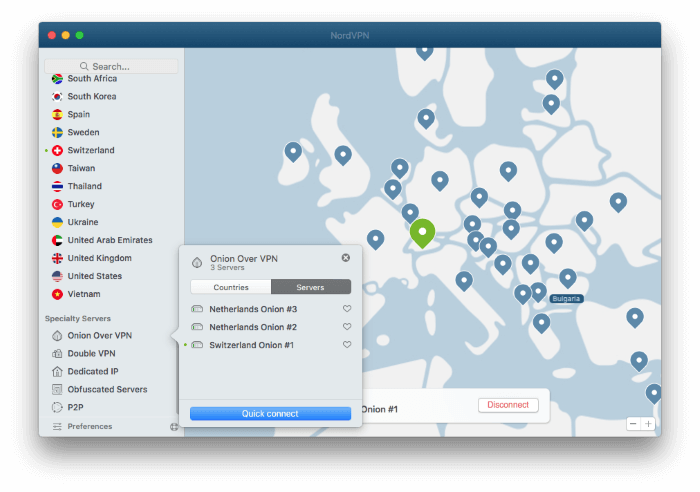
“Onion over VPN is a privacy solution where your internet traffic goes through one of our servers, passes through the Onion network, and only then reaches the internet.” (NordVPN)
ExpressVPN lists a few benefits of Onion over VPN:
- Some school and business networks block TOR. By connecting to a VPN first, you can still access it. Your ISP won’t be able to see that you’re using TOR, either.
- Your VPN provider will know that you’re using TOR but won’t be able to see your online activity through that network.
- If there’s a bug or vulnerability with the TOR browser or network, your VPN adds an extra level of security to protect you.
- It’s easier to set up: just connect to your VPN, then launch the TOR browser. Some VPNs allow you to access the TOR network while using other browsers (see below).
So What Should You Do?
If Onion over VPN offers the most private, secure online experience, why isn’t it more commonly used? Two reasons. First, it creates a significantly slower internet connection. Second, most of the time, it’s overkill. The vast majority of users don’t need that extra level of protection.
For normal internet browsing, a standard VPN or TOR connection is all you need. For most people, I recommend the use of a reputable VPN service. You’ll be able to surf the net without having every site you visit tracked and logged. Just choose a provider you can trust who offers the features you need.
We’ve written tons of articles to help you with that decision:
However, there are situations where you may choose to trade speed for the additional security of Onion over VPN, such as when privacy and anonymity are paramount.
Those choosing to bypass government censorship, journalists protecting their sources, and political activists are prime examples, as are those who have strong ideas about freedom and security.
How do you get started? You can use the Onion network with any VPN service by first connecting to the VPN and then launching the TOR browser. Some VPNs claim to offer additional support for TOR over VPN:
– NordVPN (from $3.71/month) is a fast VPN service that claims to be “fanatical about your privacy and security” and offers specialized Onion over VPN servers that will route your traffic through the TOR network without having to use the TOR browser. You can learn more from our NordVPN review.
– Astrill VPN (from $10/month) is fast, easy to use, and offers TOR over VPN with any web browser. Learn more in our Astrill VPN review.
– Surfshark (from $2.49/month) is a highly-rated VPN offering fast servers and additional security options, including TOR over VPN. The use of the TOR browser is required. Their servers use RAM rather than hard drives, so no sensitive data is retained when they are turned off. It is covered in detail in our Surfshark review.
– ExpressVPN (from $8.33/month) is a popular VPN that can tunnel through internet censorship and offers TOR over VPN (via the TOR browser) for even more stringent online privacy. We describe it in detail in our ExpressVPN review.
Note that NordVPN and Astrill VPN offer the most convenience by allowing you to access TOR while using any browser, while Surfshark and ExpressVPN require using the TOR browser.