Wireless internet seems to be ubiquitous today. Businesses provide it as a benefit to employees and customers. People provide their wireless passwords to visitors in their homes. It’s a way to keep us connected when our devices may otherwise be unable to access the internet.
Can someone such as the Wi-Fi owner see what you’re doing on the internet, even if you’re browsing in incognito mode? The answer is: yes!
I’m Aaron, a technology professional and enthusiast with 10+ years of working in cybersecurity and with technology. I’m an advocate for network security and privacy. Knowledge of how to secure your browsing and improve your privacy is the best bang-for-your-buck to keep you safe online.
In this post, I’ll explain why incognito doesn’t shroud your internet browsing, how your browsing activity can be captured by Wi-Fi providers, and what you can do to prevent that from happening.
Table of Contents
Key Takeaways
- Incognito only prevents your device from saving your browsing history.
- By virtue of the way the internet works, all downstream infrastructure captures your browsing activity.
- The only way to prevent a Wi-Fi owner from seeing your browsing activity is by using a browser specifically designed to hide that or by using a VPN.
What is Incognito?
Incognito (Chrome), InPrivate (Edge), or Private Browsing (Safari, Firefox) are internet browser options that open your internet browsing session in a session that:
- Doesn’t save your browsing history
- Doesn’t collect or save cookies to your desktop
- Prevents site trackers from associating browsing activity with your online accounts (unless you sign in with those accounts).
Those private browsing options let you open a window, browse as you would, and then close your session on the computer without saving your information to the computer. This is especially useful when you’re using a public or other shared computer and you don’t want to have your information stored on that computer.
Why Doesn’t Incognito Hide Browsing Activity from Wi-Fi Owners?
When you connect to Wi-Fi:
- your computer connects to a “wireless access point” (or WAP) which is a radio station that receives and sends data to your computer’s Wi-Fi card
- the WAP is physically connected to a router which, in turn, provides access to the internet
This is what those connections look like at a very abstract level:
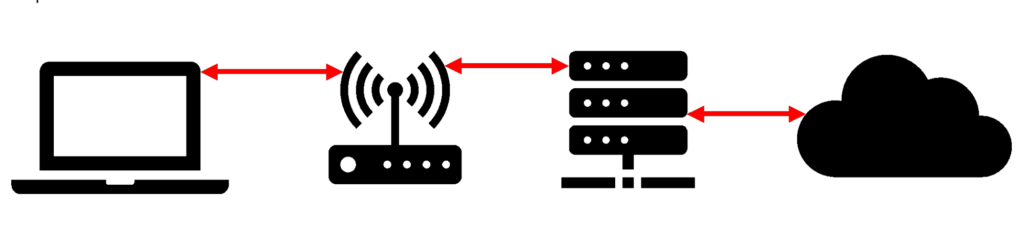
In reality, the connections are much more complex, with additional servers and routing hardware at the Internet Service Provider (ISP), Domain Name Service (DNS) broker, website hosting provider, and other ancillary services called by the website. The considerations with respect to a Wi-Fi owner extend to all those points of interaction too.
When you visit a website, you request information from that site—or rather, the servers storing that site—and those servers request information from you. Specifically, the site asks: what is your address so I can send you data?
That address is called an IP, or Internet Protocol, address. The site server asks for that data so it can send you the information you need to view the site. This happens every time you click a link, every time you stream video, or every time you listen to music online.
Where you use Wi-Fi, the router provides a public address to the world so that information can find its way back to you. Networking equipment behind the router then parses that to your computer via an internal, local IP address.
That might all seem very complex, but it’s effectively the same system we use for sending snail mail. I think that’s a good analogy for why incognito doesn’t hide your browsing activity from a Wi-Fi Owner.
When you send or receive mail, typically it has two addresses on it: the recipient’s address and the return address. It also has names and street addresses. Those addresses are the same as IP addresses. The name on the envelope allows the recipients to give the mail to the specific addressee, which is like a local IP address, while the street address allows it to be delivered to a mailbox, which is like a public IP address.
Most websites on the internet use HTTPS, which is a secure version of the HTTP protocol. That is like the envelope, which hides the specific contents of the request. So only the sender and recipient can see inside, but everyone knows who’s sending what and where. Some groups along the chain, like USPS, FedEx, UPS, and DHL even take photos of that information! That’s like log files on a server, which record activity on the server.
Every time you visit a website or click a link, you’re effectively sending a letter asking for different content back. The website then provides you with that content. Incognito mode effectively lets you shred all of the letters and envelopes you receive at the end of the browsing session when you close the window. It doesn’t remove the ability for intermediaries between you and the website from recording what requests you made and when.
So not only can a Wi-Fi owner see your browsing activity, but they may also even be recording it. For corporate Wi-Fi, that is a de facto standard. For public or home Wi-Fi, that may be less prevalent. I personally use a Raspberry Pi with PiHole on my home network for ad blocking. One of the features that have is recording browsing traffic.
How Do You Hide Browsing Activity from Wi-Fi Owners?
There are a couple of easy ways to accomplish this. While I’m not going to provide a How-To on how to do that here, I will provide information about how those technologies hide browsing activity from a Wi-Fi Owner.
Method 1: Using a Browser like Tor
Tor browser, also known as an onion browser, uses peer-to-peer connectivity to hide browsing activity. Tor creates a secure addressing network, so all requests go to and come back from the Tor network.
Other members of the Tor network can theoretically see your browsing activity, but that browsing activity is hidden beneath numerous layers of transmissions making it very difficult to do so.
Using the letter analogy, you send a letter inside of a letter addressed to Tor. Tor then sends it to someone else, who sends it to someone else, and so on. Eventually, someone along the line sends it back to Tor to open everything up and send the original letter inside to the target website.
Method 2: Using a VPN
VPN, or Virtual Private Network, is a way for you to hide your identity on the internet. It works by creating a secure connection between your computer or mobile device and a server somewhere in the world.
All your internet traffic, then, is routed through that server. The server then asks for data from websites on your behalf and provides its address to those sites. It then relays the information back to you over that secure connection.
What the Wi-Fi owner would see is your letters to and from the VPN server, with the actual website request and response hidden in the letter.
Conclusion
Wi-Fi owners (and other intermediaries) can see what sites you visit, even if you use incognito mode.
You need to escalate your privacy and security practices in order to stop that. A couple of options are Tor or onion browsers and VPN. There are pros and cons with those services too, so before doing that, really think about why you want to hide your browsing activities and how best to accomplish that.
Do you use Tor or VPN? What other practices do you have to improve your online privacy? Let me know below!
